Problem Statement
Decentralized lending protocols today expose sensitive borrower data (collateral amounts, credit metrics) on-chain, creating privacy risks and disincentivizing participation. At the same time, real-time risk assessment and dynamic interest-rate adjustments are hindered by oracle latency and lack of verifiable proofs, leading to delayed liquidations or inaccurate collateralization. These issues primarily affect borrowers, lenders, and protocol designers seeking efficient, private, and trustless borrowing/lending experiences.
Solution Overview
ZeroEyes+ Private Money Market delivers a privacy-first, AI-driven lending framework on Layer 2 that combines zkSNARK-based risk scoring, Pyth Network’s sub-second price feeds, and Alith’s MPC co-agent automation—all accessed via gasless EIP-7702 meta-transactions. By encrypting borrower data client-side, running quantized AI models off-chain, generating succinct zero-knowledge proofs, and verifying them on Hyperion L2 in under one second, the protocol enables instantaneous collateral updates, dynamic interest rates, and secure liquidations without ever revealing raw borrower information.
This approach is uniquely innovative because it merges advanced zkML techniques, high-frequency oracles, and autonomous MPC execution—creating a next-generation money market that is both private and provably correct.
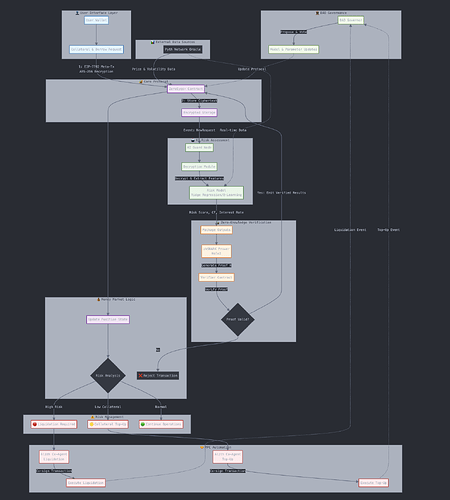
Project Description
ZeroEyes+ Private Money Market is architected as a modular Layer 2 protocol built on Hyperion (Metis L2). Users begin by encrypting their collateral and off-chain credit metrics (e.g., on-chain holdings and encrypted third-party credit scores) via AES-256 and submitting them through an EIP-7702 meta-transaction, which sponsors gas costs for a seamless UX.
The protocol’s AI Guard network, comprised of permissioned nodes, retrieves Pyth’s real-time price and volatility feeds (updated every ~400 ms) and decrypts submitted data to run quantized risk models—such as Ridge Regression for creditworthiness and a Q-Learning agent for dynamic rate recommendations. Each inference generates a succinct Halo2 zkSNARK proof (< 12 KB) attesting to the correct execution of the model against committed weights and real-time oracle inputs.
The Hyperion L2 verifier smart contract checks these proofs in under one second, immediately updating each user’s collateral factor (LTV ratio) and interest rate in the protocol’s on-chain state. If a borrower’s risk score crosses a predefined threshold, ZeroEyes+ emits a “liquidation” event that Alith’s MPC co-agent network automatically co-signs and executes a decentralized liquidation transaction—ensuring immediate, trustless action without centralized intervention. Borrowers benefit from privacy by default, lenders enjoy real-time collateral security, and protocol designers gain a fully upgradable framework: model hashes and verifying keys can be replaced via on-chain governance without redeploying core contracts.
This synergetic combination of zkML, high-frequency oracles, and MPC automation excites us because it demonstrates a viable path to truly private, low-latency, and provably secure DeFi money markets—paving the way for broader financial on-chain innovations.
Before vs. ZeroEyes+ Private Money Market
| Metric | Traditional DeFi Lend/Borrow | ZeroEyes+ Private Money Market |
|---|---|---|
| Privacy | Collateral and credit data fully public on-chain | AES-encrypted until zkSNARK proof verifies correctness |
| Oracle Latency | 1–3 second batched price updates | Sub-second Pyth real-time feeds (~400 ms per update) |
| Risk Proofs | None (off-chain risk engines) | zkSNARK-attested on-chain proofs (<12 KB, <1 s verify) |
| Collateral Safety | Manual or delayed liquidations | Automated via MPC co-agent in <1 s on threshold breach |
| Gas Costs | High L1 fees + on-chain oracle fees | L2 gas (~0.00024 ETH) + batched batch-verified proofs |
Community Engagement Features
| Task | Points | Description |
|---|---|---|
| Encrypted Borrow Request | 20 pts | Submit a private borrowing transaction (AES-encrypted collateral + meta-tx) |
| Latency Benchmark | 30 pts | Measure end-to-end time (meta-tx → proof verify → state update) and submit results |
| Model Tuning Proposal | 40 pts | Suggest improvements to quantized risk model parameters or offer new feature-engineering ideas |
| zk Circuit Security Audit | 50 pts | Identify potential edge-cases or inefficiencies in the zk circuit constraints |
| Alith Automation Demo | 60 pts | Build and share a sample front-end or script demonstrating a liquidity trigger via Alith |
- Points System & Rewards:
- Each task earns “XP” points redeemable for gas credits, early access to private testnets, and “ZeroEyes Guardian” badges (soulbound NFTs) that confer governance weight.
- Weekly leaderboard rankings foster friendly competition.
- Gamification & On-Boarding:
- Completed tasks unlock incremental badges (e.g., “Latency Learner,” “Model Master”), encouraging deeper engagement and knowledge sharing.
- Clear, step-by-step tutorials (e.g., “Encrypt → Borrow → Verify”) guide newcomers, rewarding them with points at each milestone to flatten the learning curve.
- Community-Driven Improvement:
- Top contributors are invited to quarterly “zkRisk Sprints,” working directly with the core team on circuit optimizations or new model integrations, further aligning the protocol’s evolution with user feedback.
Getting Involved
- **GitHub & Documentation (https://github.com/ZeroEyesPlus not yet!) for smart contracts, zkSNARK circuits, AI Guard code, and SDK examples.
- Community Link: Join the ZeroEyes+ Telegram community at https://t.me/+e1iLoIURqK84NzRl for real-time discussion, issue reporting, and collaboration.
- Discord: Participate in the
#zeroeyes-pluschannel on the HyperHack Discord server to ask questions, coordinate bounties, or share demos. - Bounties & Grants: Contribute new quantized risk models, optimize zk proof size, build Alith MPC workflows, or develop front-end integrations to earn token grants and governance tokens.
Co-Founder Team : @Alice_Waldolf