Sentinel: Real-Time Smart Contract Defense Layer for Metis Hyperion
Problem Statement
Smart contract exploits are costing the ecosystem billions — and it’s not because developers don’t care about security. It’s because the tools to proactively defend against live attacks simply don’t exist. Audits are static, expensive, and quickly outdated. Most teams are forced to choose between shipping fast or staying safe. That’s the real tradeoff we want to destroy.
Solution Overview
Sentinel is a real-time smart contract defense layer built natively for the Metis Hyperion stack. Think of it like a firewall and AI auditor for your dApps — detecting threats, scoring risks, and rerouting execution before exploits drain your contracts. It’s modular, trustless, and privacy-preserving by design.
What makes Sentinel different is it doesn’t just audit contracts after they’re built — it actively protects them while they run, leveraging encrypted mempools, ZK proofs, and a self-healing mechanism that respects immutability.
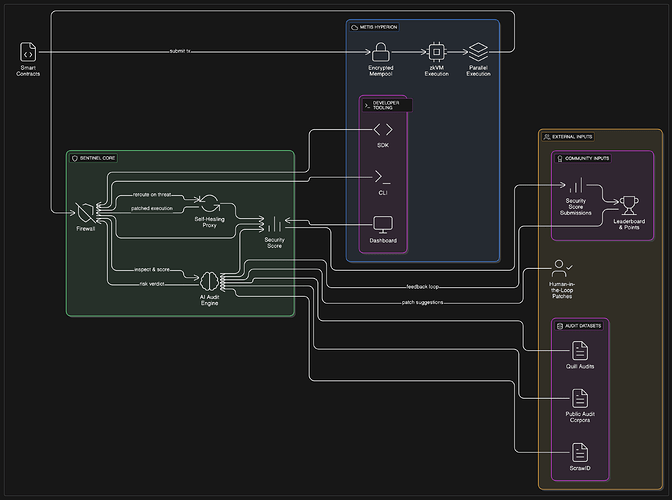
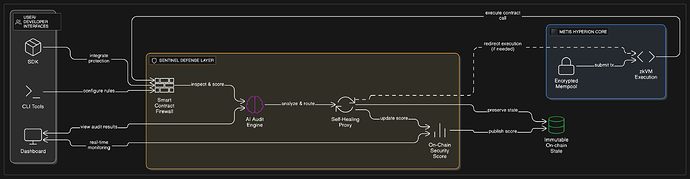
Architecture Overview
Project Description
Sentinel is a Web3-native security layer that plugs into smart contracts without requiring devs to rewrite them. Its core features include:
- AI-Powered Audit Engine trained on datasets from Quill Audits, ScrawID, and public audit corpora.
- Smart Contract Firewall that inspects and filters transaction behaviors in real time.
- Self-Healing Contracts that redirect execution to patched logic without mutating on-chain state.
- On-Chain Security Score to build user trust and prove protocol integrity.
We’re building on Metis Hyperion because of its:
- Encrypted mempool and zkVM execution environment
- Parallel execution support
- Modular, developer-friendly architecture
Developers interact with Sentinel via CLI tools, SDKs, or dashboards — making it easy to integrate security into existing workflows.
What excites us? We’re flipping the paradigm — from audits as a checkbox to security as a continuous, runtime service.
Community Engagement Features
We’re turning smart contract security into a game.
Points System
- Earn points on-chain
- Redeem them for Sentinel access, merch, NFTs, or governance perks
- Leaderboard for most secure builders
Why It Works
This incentivizes adoption through a feedback loop:
- Teams secure their projects
- Users learn by testing
- Communities gain trust
Getting Involved
Sentinel is more than a tool — it’s a movement to make Web3 safer by default.
Here’s how you can contribute:
- Developers: Build the CLI, SDK, and score dashboard
- AI Hackers: Train and tune models with audit data
- Security Experts: Join our DAO to review patches and audit logic
- Community Creators: Educate, test, promote — be part of the mission
Interested? DM me
Diagram Space
What’s Next?
For this hackathon, we’re focusing on shipping an AI-powered audit engine with 1–2 of the above features. Long-term, Sentinel will evolve into a full-blown security operating layer for Metis and beyond.
Together, we can make Web3 unbreakable.